AVESTA: Research

Project:
NSF EAGER: Sonifying Cyber-Security Cues for Internet Users Who Are Visually Impaired
Some Quick Facts About the Project:
- Sponsor: National Science Foundation (NSF) in 2013
- Title: EAGER: Secure and Trustworthy Computing (SaTC): Sonifying Cyber-Security Cues for Internet Users Who Are Visually Impaired, National Science Foundation (NSF) (NSF Project Summary). Awarded August 2013, $157,783.00. The project is for one year. This project investigates the effects of auditory perceptions of security cues on the Internet users who are visually impaired.
- Type: A multidisciplinrary project
- Involved Departments: Computer Science, Psychology, Music, and Education (Texas Tech University)
- Project Investigators:
- Dr. Akbar Siami Namin, PI, Computer Science, Texas Tech University
- Dr. Rattikorn Hewett, Co-PI, Computer Science, Texas Tech University
- Dr. Yualin Zhang, Co-PI, Computer Science, Texas Tech University
- Dr. Keith S. Jones, Co-PI, Psychology Department, Texas Tech University
- Dr. Fethi Inan, Co-PI, College of Education, Texas Tech University
- Dr. Rona Pogrund, Senior Member, Texas School for the Blind and Visually Impaired, Austin
- Dr. Thomas Hughes, Senior Member, Department of Music, Texas Tech University
- Dr. Gary Forsythe, Consultant, Department of History, Texas Tech University
- Jeff Mozlow, External Consultant
- Prerit Datta, Graduate Research Assistant, Computer Science
- Alaa Darabseh, Graduate Research Assistant, Computer Science
- John Rose, Graduate Research Assistant, Texas School for the Blind and Visually Impaired
- Miriam Armstrong, Graduate Research Assistant, Psychology
- Sandesh Bhattarai, Undergraduate Research Assistant, Computer Science
- Benjamin Albot, Undergraduate Research Assistant, Computer Science
- Avesta Hojjati, Undergraduate Research Assistant, Computer Science
- Neil Imbery, Undergraduate Research Assistant, Education
- Tofunmi Salau, Undergraduate Research Assistant, Education
- Other Facts:
-
The work received the "Distinguished Poster Award" at The ACM/USENIXSymposium on Usable Privacy and Security (SOUPS 2016), 2016, Denver, CO, USA. [ACM/USENIX Distinguished Poster Award]
-
Motivation & Research Goals
It is estimated that more than 20 million of Americans are living with some vision problem of which 10 million are totally blind. The Internet has offered opportunities to broaden the lives of individuals who are blind and visually impaired in education, employment, and socialization, in a way never seen before. However, security and privacy issues have become a great barrier to Internet use for persons who are visually impaired.
In this early concept and explanatory project, The project investigators propose to sonify security concerns and cues for users with visual disability by:
- Investigating human factors in security and usability to determine security challenges of visually impaired
- Conducting research on sonification of security cues and presenting security and privacy information
- Building usability testing artifacts for evaluating sonification-based Internet browsing
- Conducting usability testing and evaluating the proposed sonified environment
Sonifying Security Threats, Concerns, and Cues
The following figure illustrates the idea of sonifying security threats/cues. There may be several places on the Internet, local computer systems, and application levels that may have some security holes and thus may be target for attacks. The idea is to detect these concerns and translate them into effective sounds to quickly convey the potential risks and concerns.
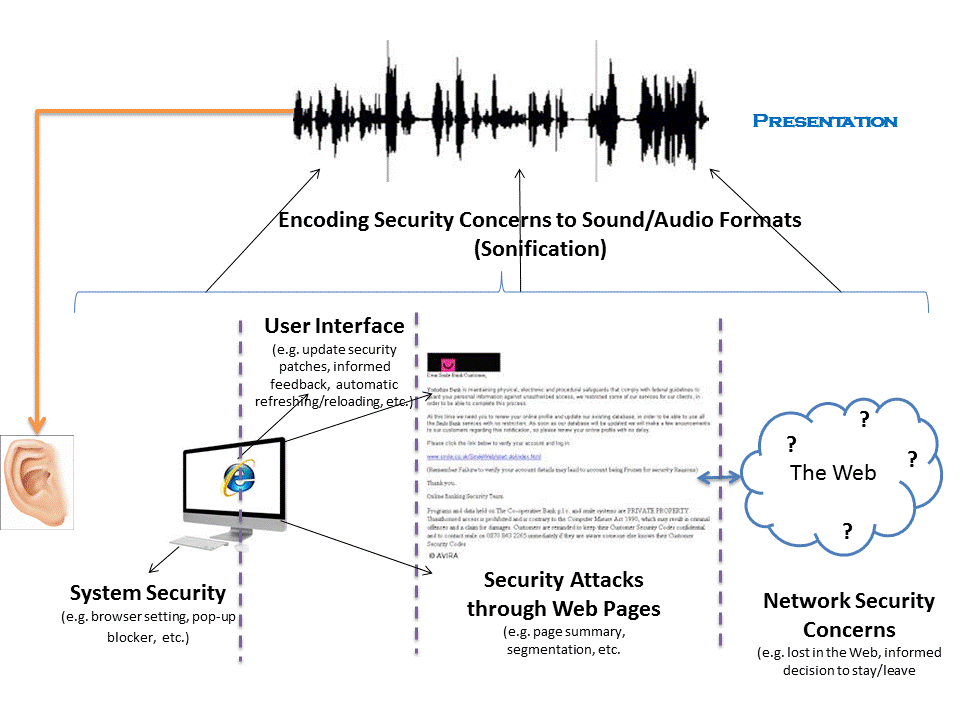
The following figure illustrates the possible cyber-threats applicable for users who are visually impaired. The sonification translates the security settings data into audio formats to the users, while reducing the possibility of overwhelming the user with massive text data read by screen readers. The proposed project involves novel research to identify appropriate presentations including sonic and phonetic tones to represent security warnings.
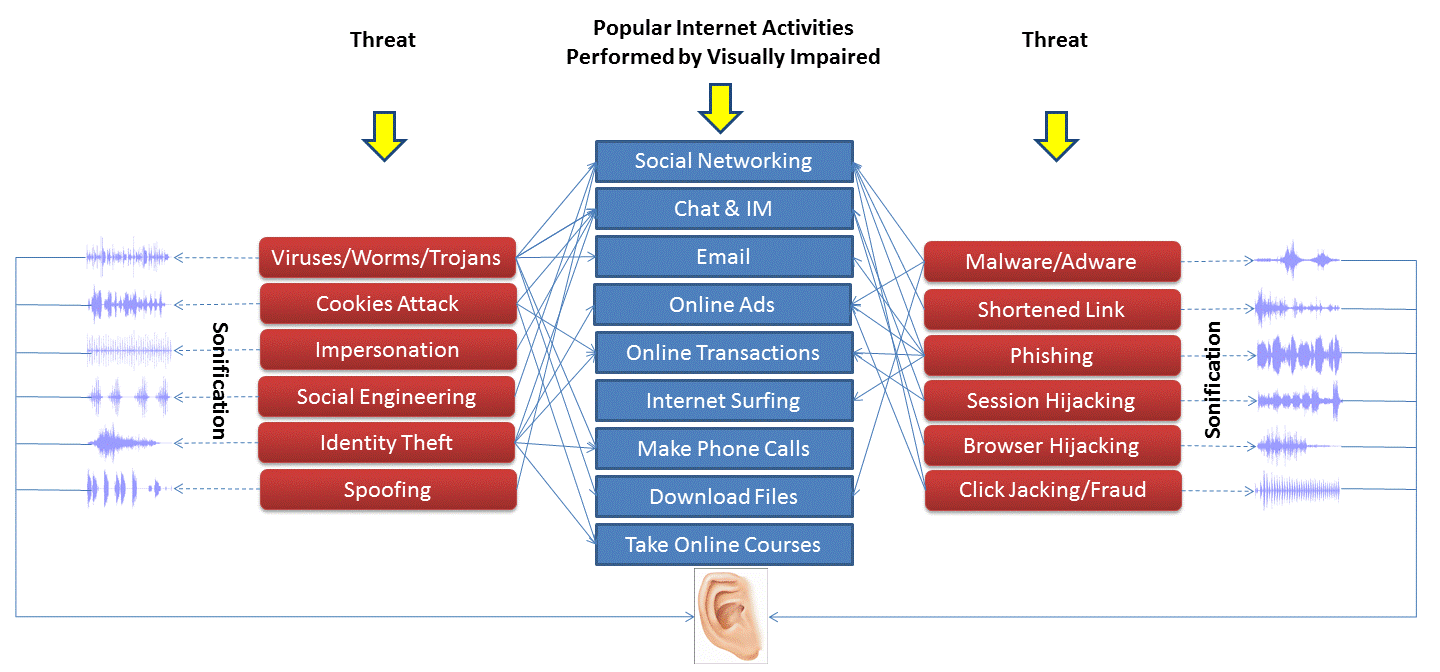
The project consists of several stages. Since most of the research results are under submissions for publications, the parts of the project that are published or accepted for publications are reported here. This Web page will be updated as soon as the results are published.
Stage 1. Underestanding Security Issues Relevant to the Users with Visual Impairements
To understand the security issues, a survey with several questions was designed to collect data on:
- User Characteristics
- The Internet Use
- Cyber-security Threats
- Needs and Expectations
The survey was conducted in an ethical, trustful, and respectful manner to ensure the fruitful collaboration between project investigators and the participants. To avoid accessibility issues regarding conducting surveys, we employed various data collection methods and strategies (online/onsite/phone survey, For detailed results, please refer to the following paper which has been accepted for publications in
Fethi Inan, Akbar Siami Namin, Keith S. Jones, and Rona Pogrund, (2015). Exploring Internet Use of Individuals with Visual Impairments. Educational Technology & Society" (ISSN 1436-4522) [Journal indexed in Social Sciences Citation Index (listed in Web of Science)]. Accepted. [Paper].
This material is presented to ensure timely dissemination of scholarly and technical work. Copyright and all rights therein are
retained by authors or by other copyright holders. All persons copying this material must adhere to the terms of the relevant
copyrights.
Stage 2. Sonifying Security and Privacy Information
1) The preliminary results of the research is publihsed at ACM International Conference on Computer-Human Interactions (ACM CHI'16), the Late-Breaking Work track. The ACM CHI is a top venue conference in the area of human-computer interactions and it is considered to be the most prestigous venue in this area.
Akbar Siami Namin, Rattikorn Hewett, Keith S. Jones, and Rona Pogrund (2016).Sonifying Internet Security Threats. The ACM International Conference on Computer-Human Interactions (ACM CHI'16), 2016, San Jose, CA, USA. [Paper] [Poster].
2) Another part of the work is also presented and publihsed at ACM/USENIX Twelfth International Symposium on Usable Privacy and Security (SOUPS 2016), Denver, CO, 2016. The workshop was held in conjunction with the USENIX Security 2016 Conference, a top venue conference in the area of security.
Akbar Siami Namin, Rattikorn Hewett, Keith S. Jones, and Rona Pogrund (2016).The sounds of Cyber Threats. The ACM/USENIXSymposium on Usable Privacy and Security (SOUPS 2016), 2016, Denver, CO, USA. [Paper] [Poster].
The work received the "Distinguished Poster Award." [ACM/USENIX Distinguished Poster Award]

This material is presented to ensure timely dissemination of scholarly and technical work. Copyright and all rights therein are
retained by authors or by other copyright holders. All persons copying this material must adhere to the terms of the relevant
copyrights.
Stage 3. Usability Testing and the Final Results
Under review for publications.
Sonifications Artifact
You can find the sonifications, i.e., natural sounds, of three cyber security threats here [Sounds]:- Phishing
- Malvertising
- Form-filling
This material is presented to ensure timely dissemination of scholarly and technical work. Copyright and all rights therein are
retained by authors or by other copyright holders. All persons copying this material must adhere to the terms of the relevant
copyrights.
Usability Testing Artifact
You can find the usability testing artifacts, Web applications, here [Web Applications].- An Online and Simple Banking System with Form-filling Concern
- An Online Pet Shop with Malvertising Attack
- A Tech News Portal with Phishing Attack
This material is presented to ensure timely dissemination of scholarly and technical work. Copyright and all rights therein are
retained by authors or by other copyright holders. All persons copying this material must adhere to the terms of the relevant
copyrights.
KeepSafe: A Sonification Sandbox (Chrome Extension)
You can download KeepSafe here [KeepSafe: A Sonification Sandbox], [Installation Guide]. Consent form for conducting usability testing [Consent Form]. Scenarios for for conducting usability testing[Scenarios for Usability Testing]- A paper has been submitted for publication and it is under review.
This material is presented to ensure timely dissemination of scholarly and technical work. Copyright and all rights therein are
retained by authors or by other copyright holders. All persons copying this material must adhere to the terms of the relevant
copyrights.




