AVESTA: Research
A video introducing the project, its objectives, and potential impacts.


Project:
NSF SaTC: Medium: User-Centric Design of a Sonification System for Automatically Alarming Security Threats and Impact
Some Quick Facts About the Project:
- Sponsor: National Science Foundation (NSF) in 2016
- Title: NSF SaTC: Medium: User-Centric Design of a Sonification System for Automatically Alarming Security Threats and Impact Impaired, National Science Foundation (NSF) (NSF Project Summary). Awarded August 2016, $889,150.00. The project is for four years. It creates two repositories: i) a repository of sounds tagged with emotional impacts, and ii) a repository of cyber threats tagged with users' concerns and consequences. The linkage between two repositories will build an automated sonification system where security threats are linked to representative sounds.
- Type: A multidisciplinrary project
- Involved Departments: Computer Science, Psychology, Music, and Education (Texas Tech University)
- Project Investigators:
- Dr. Akbar Siami Namin, PI, Computer Science, Texas Tech University
- Dr. Keith S. Jones, Co-PI, Psychology Department, Texas Tech University
- Dr. Rattikorn Hewett, Co-PI, Computer Science, Texas Tech University
- Dr. Thomas Hughes, Senior Member, Department of Music, Texas Tech University
- Dr. Rona Pogrund, Senior Member, Texas School for the Blind and Visually Impaired, Austin
- Ben Widlus, Graduate Research Assistant, Psychology Department
- Sara Sartoli, Graduate Research Assistant, Computer Science
- Prerit Datta, Graduate Research Assistant, Computer Science
- Other Facts:
-
This grant is a follow-up of the following grant:
NSF EAGER: Sonifying Cyber-Security Cues for Internet Users Who Are Visually Impaired
-
This grant is a follow-up of the following grant:
Motivation & Research Goals
The Internet has become an integral part of everyday life. The great benefits of the Internet also come with potential risks, security issues, and privacy concerns. Internet security products are usually employed to inform users about security incidents. There are three major problems using these security products:
- these tools often overwhelm users with a great many features making their usability a serious issue,
- these tools are not always accessible to every type of user such as those who are visually impaired,
- most of the Internet users are unfamiliar with various types of security threats and thus their impacts.
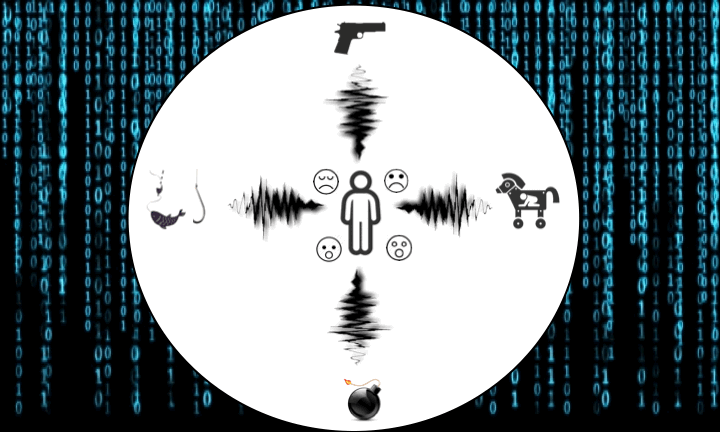
This project translates security warnings and threats into various forms of sounds. The introduced user-centric sonification takes a security warning and maps out the risks and consequences associated with the underlying security threat into a certain type of sound that reflects the emotional feelings of the potential risks and harm caused by the threat.
- The project builds a repository of sounds tagged with their emotional impacts such as fear, happiness, and sadness.
- The project also builds a second repository of security threats tagged with similar emotional impacts such as fear of loss of sensitive information, impersonation, and privacy exposure.
The constructed repositories can be useful for music and computer security industries such as Amazon, anti-virus software developers, and producers of major Web browsers. The sonification-based technology for translating security warnings to sounds can be integrated into any popular Internet Web browsers. The project will have direct impact on the development of technologies that enhance accessibility for Internet users who are visually impaired and will increase their Internet safety.
Still to Come ...
Stages.
Under review for publications.
- A paper has been submitted for publication and it is under review.
This material is presented to ensure timely dissemination of scholarly and technical work. Copyright and all rights therein are
retained by authors or by other copyright holders. All persons copying this material must adhere to the terms of the relevant
copyrights.




